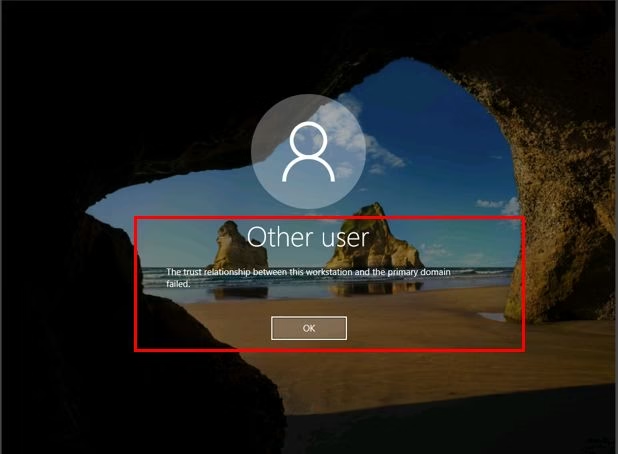
Active Directory (AD) trust relationship issues can be a significant roadblock in maintaining a seamless IT environment. These problems often manifest as the dreaded error message: “The trust relationship between this workstation and the primary domain failed.” From my experience, addressing these issues promptly is crucial to ensure uninterrupted access and security within your network.

Understanding the Root Cause
At the heart of this problem lies a mismatch between the computer’s password stored in its local system and the one stored in the AD. This discrepancy can arise from various scenarios, such as restoring a computer from an outdated backup, cloning systems without proper preparation, or even prolonged disuse of a machine. When the system detects this mismatch, it severs the trust relationship, leading to authentication failures.
Effective Methods to Restore Trust
Method 1: Disjoin and Rejoin Domain
- Reestablishing Domain Membership
- Disjoin from Domain: Log in with local administrative rights. Execute:
dsjoin /leave- Restart the Computer: A reboot ensures all changes take effect.
dsjoin /domain Domain Name /user Domain Admin User /passwords *- Final Restart: This solidifies the domain reattachment.
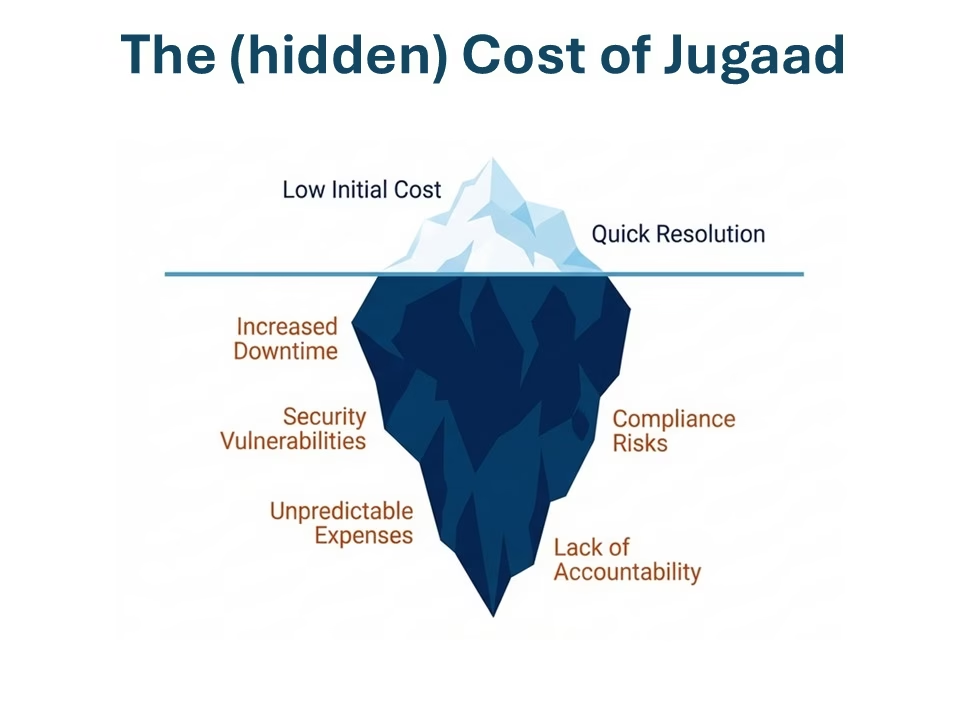
While this method is thorough, it can be time-consuming due to multiple reboots.
Method 2: Fix Trust through PowerShell
- Log in locally and execute:
Test-ComputerSecureChannel -Repair -Credential DomainName\Administrator- Restart the Computer: This ensures the repair is applied.
This approach is efficient and often resolves the issue without necessitating a domain rejoin.
Method 3: Reset Computer Password (PowerShell)
- Execute Reset Command: Log in with local admin rights and run:
Reset-ComputerMachinePassword -Server DomainController -Credential DomainName\Administrator- Restart the Computer: To apply the new password settings.
This method directly addresses the password mismatch causing the trust issue.
Method 4: Reset Secure Channel (Netdom)
- Reset Secure Channel: Log in as a local admin and execute:
netdom resetpwd /Server:DomainController /UserD:DomainAdmin /PasswordD:*- Restart the Computer: To finalize the reset process.
Netdom is a command-line tool that can effectively reset the secure channel between the workstation and the domain.
Method 5: Delete & Recreate Computer in AD
- Delete the computer object from Active Directory Users & Computers (ADUC).
- Open PowerShell as local admin and remove the computer from the domain:
Remove-Computer -UnjoinDomainCredential DomainName\Administrator -PassThru -Verbose- Restart the computer.
- Rejoin the domain:
Add-Computer -DomainName "DomainName" -Credential DomainName\Administrator -Restart- Restart again.
Method 6: Check & Sync Time
- Resynchronize Time: Log in locally and run:
w32tm /resync- Manual Time Sync (if needed): If issues persist, execute:
w32tm /config /manualpeerlist:"time.windows.com" /syncfromflags:manual /update- Restart the Computer: To ensure time settings are applied.
Time discrepancies between a workstation and the domain controller can lead to trust issues; ensuring synchronized time is a simple yet effective troubleshooting step.
Why Choose Tech-AD for Your Active Directory Needs?
Navigating Active Directory challenges can be daunting. At Tech-Ad, we specialize in providing tailored solutions to ensure your network remains robust and secure. Our services include:
- Expert Troubleshooting: Swift identification and resolution of AD trust issues.
- Proactive Monitoring: Regular health checks to prevent potential disruptions, covered in our Annual Maintenance Contract.
- Comprehensive Support: Guidance and assistance through every step of the remediation process.
Don’t let trust relationship problems hinder your operations. Reach out to Tech-Ad today, and let our expertise work for you.

Leave a Reply